Netgear Nighthawk RAX40
It's finally running after a full hack and crack break in and rearranging its internal software. Zero help from Netgear support. There are serious privacy concerns about the data this router is collecting and sending back to "the cloud". Netgear's privacy statement clearly spells this out, however it is not disclosed in the marketing literature.
 I wanted a wireless AP (Access Point) that would handle the demands of AppleTV 4K, lots of phones, computers and IoT devices that are congregating at the north end of the house. I had a 15 year old Netgear AP, which was still running fine out in the garage. So I took a look at Netgear's latest stuff with the new WiFi Gen 6.
I wanted a wireless AP (Access Point) that would handle the demands of AppleTV 4K, lots of phones, computers and IoT devices that are congregating at the north end of the house. I had a 15 year old Netgear AP, which was still running fine out in the garage. So I took a look at Netgear's latest stuff with the new WiFi Gen 6.
After buying the RAX40 at a non-discount price ('cause it's "still new", according to the sales assistant), I managed to set it up in "Access Point" mode. But to my horror, a couple of days later it crashed. Dead. Dead dead. Well not brick dead but power cycle at the power point dead. And every 24 to 48 hours. Reset button did nothing. Power button did nothing. What a waste of time Netgear support was too.... :-(
Then, to make things worse, I discovered it was spying on me! PiHole revealed lots of DNS requests to a series of Netgear sites.
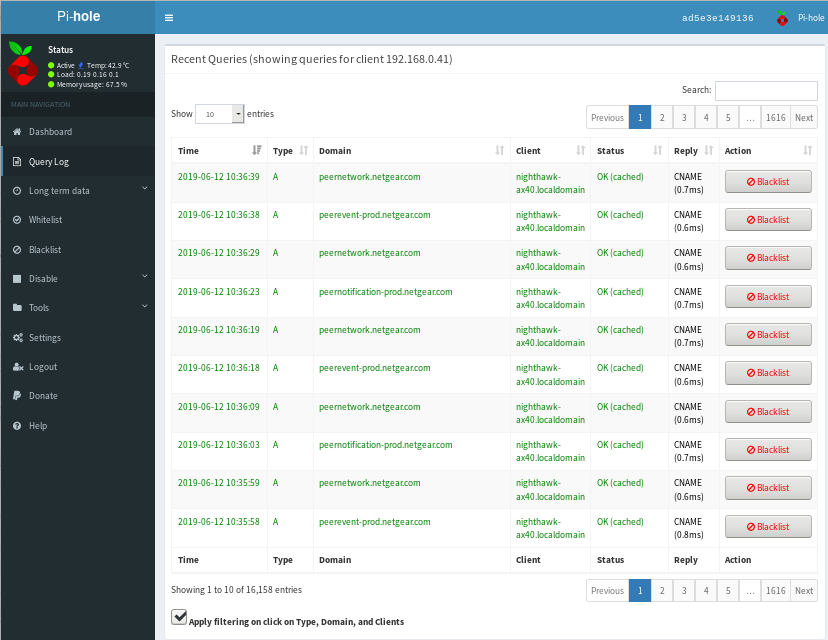
The rest of this page describes how to hack in to your Nighthawk RAX40 (but probably all Nighthawk models) and kill off offending software. The fact that undocumented telnet access is even possible is something of a remarkable feature for Netgear routers. Having to use it is total bullshit! Non-technical people have absolutely no chance of doing this.
I'm pretty sure Netgear is not the only vendor spying on its users. Without a doubt Chinese products are certainly doing the same thing but sending your data back to China for analysis.
WARNING: proceeding past here may damage your router!
Some of the sites the RAX40 attempted to access include:
a1599er83nvyl8.iot.us-west-2.amazonaws.com
www.netgear.com every hour on the hour
http.fw.updates1.netgear.com
registration.ngxcld.com
updates1.netgear.com
updates2.netgear.com
updates3.netgear.com
updates3.netgear.com.localdomain
Comprehensive hardware teardown (Chinese Style - excellent!)
随着各大厂商AX的路由的不断普及,网件终于也带来了旗下的AX路由。本次要为大家介绍的是网件夜鹰AX4( 官网链接),夜鹰AX4采用新一代 Wi-Fi 6 技术,可为所有连接设备提供更强大的网络容量以及始终如一的强大信号强度。下面来看看它的具体表现
http://koolshare.cn/thread-160534-1-1.html
Howto Login to Netgear Nighthawk RAX40
update: I've had to downgrade the RAX40 software back to Firmware Version V1.0.2.46_1.0.1 as later versions fixed this hack.
I did not attempt to access the router in its normal operating mode from the internet using this technique. However, it might work, who knows?
https://oldwiki.archive.openwrt.org/toh/netgear/telnet.console
Download telnetenable-0.4-2.tar.gz from:
http://www.myopenrouter.com/downloads/file/3032/telnetenable-0.4-2.tar.gz
./telnetenable.linux - 020C6BA41234 admin password | nc -u 192.168.0.241 23; telnet 192.168.0.241Trying 192.168.0.41... Connected to 192.168.0.41. Escape character is '^]'. RAX40 login: admin Password:BusyBox v1.17.1 (2019-05-03 11:43:06 CST) built-in shell (ash) Enter 'help' for a list of built-in commands.+---------------------------------------------+ | Lantiq UGW Software UGW-7.5.1 on XRX500 CPE | +---------------------------------------------+root@RAX40:~#
LeafP2P
The cause of continuous DNS requests.
I settled on complete deletion of its code directory. The only problem is it comes back on every reboot, since the run image is extracted from the firmware "ROM". The only sustainable solution is to load a customized image with this code directory removed.
While this sounds impossible, there are custom third party images for other Netgear routers. For some people this might actually be a key feature. It could be the only way to guarantee information privacy and security.
However, at the time of writing there is no custom image available for the RAX40.
xgenie_remote_certificate=/opt/xagent/certs/ca-bundle-mega.crt
x_handler_1003=/opt/xagent/genie_handler
genie_soap_port=5000
lan_ipaddr=192.168.1.1
x_claimed_url=https://registration.ngxcld.com/registration/status
x_register_url=https://registration.ngxcld.com/registration/register
x_advisor_url=https://advisor.ngxcld.com/advisor/direct
x_discovery_url=https://presence.ngxcld.com/presence/presence
genie_remote_url=https://genieremote.netgear.com/genie-remote/claimDevice
readycloud_fetch_url=http://readycloud.netgear.com/device/entry
readycloud_hook_url=http://readycloud.netgear.com/device/hook
readycloud_upload_url=http://readycloud.netgear.com/directio
readycloud_use_xcloud=1
x_handler_1004=127.0.0.1:10101
rcagent_path=/opt/rcagent
readycloud_control_path=/opt/rcagent/scripts
remote_path=/opt/
remote
genie_remote_handler_log_level=1
genie_remote_cgi_log_level=1
rcagent_log_level=debug
rcagent_log_to_file=1
leafp2p_remote_url=http://peernetwork.netgear.com/peernetwork/services/LeafNetsWebServiceV2
leafp2p_service_0=RouterRemote,0,1,1,1,1,6:135,6:136,6:137,6:138,6:139,6:445,6:548,17:135,17:136,17:137,17:138,17:139,17:445,17:548
leafp2p_replication_url=https://readyshare.netgear.com/device/entry
leafp2p_run=1
leafp2p_sys_prefix=/opt/remoteleafp2p_rescan_devices=1
leafp2p_debug=1
leafp2p_path=/opt/leafp2p
leafp2p_replication_hook_url=https://readyshare.netgear.com/device/hook
leafp2p_firewall=0
leafp2p_services=1
x_http_request_timeout=
x_http_connect_timeout=
x_register_delay=
x_discovery_delay=
x_claim_delay=
x_claim_check=
x_advisor_delay=
x_xbroker_delay=
x_agent_id=GX8T88FM-XXXX-XXX-XXXXXXXXX
x_agent_claim_code=56C34CQZ7KTRZYA9NEPZMW9C
x_agent_registered=1
x_agent_claimed=
x_use_discovery=
x_register_aggressive_time=
x_xcloud_use_proxy=
x_agent_handler_name=
x_handler_event_sink=
leafp2p_username=RAX40_7pUto_XXXXXXXXXXXX
leafp2p_password=!211B3AB12E112dCn1!
leafp2p_connection_mtu=
leafp2p_websvc_host=
leafp2p_strict_connection=
leafp2p_prefer_lan_connection=
leafp2p_preferred_interface=
leafp2p_connection_method_type=
leafp2p_connection_try_mask=
leafp2p_plain_service_connection=
leafp2p_peer_route_type=
leafp2p_scripts_folder_name=
leafp2p_report_as_lan_connection=
leafp2p_log_type=
leafp2p_log_file_name=
leafp2p_log_entry_limit=
leafp2p_log_entry_flush=CPU
system type : GRX500 rev 1.2 machine : EASY350 ANYWAN (GRX350) Router model processor : 0 cpu model : MIPS interAptiv V2.0 cpu MHz : 800.000 BogoMIPS : 513.63 wait instruction : yes microsecond timers : yes tlb_entries : 32 extra interrupt vector : yes hardware watchpoint : yes, count: 4, address/irw mask: [0x0ffc, 0x0ffc, 0x0ffb, 0x0ffb] isa : mips1 mips2 mips32r1 mips32r2 ASEs implemented : dsp mt eva shadow register sets : 1 kscratch registers : 0 core : 0 VPE : 0 VCED exceptions : not available VCEI exceptions : not available
IoT Reporting
IoT (Internet of Things) reporting is based on Amazon AWS IoT CORE.
The RAX40 model uses a program named /usr/bin/ntgr_ra_dce to communicate.
Running the program with --help provides a basic guide to its functionality:
root@RAX40:~# /usr/bin/ntgr_ra_dce -help
usage: /usr/bin/ntgr_ra_dce [options]
Options are:
-p,
--period <sec> Set the period interal.
-t,
--times <times> set how many times to execute.
-v,
--version Display the version.
-P,
--printdata data Print specific data.
RA_DATA_routerHardware=0
RA_DATA_routerInfo=1
RA_DATA_routerConfig=2
RA_DATA_readyShare=3
RA_DATA_mediaDevice=4
RA_DATA_connectedDevice=5
RA_DATA_memoryInfo=6
RA_DATA_cpuUtilizations=7
RA_DATA_trafficMeter=8
RA_DATA_kernelReboot=9
RA_DATA_wifiAnalytics=10
RA_DATA_paParameters=11
RA_DATA_chanimStats=12
RA_DATA_wifiAssociatedStationInfo=13
RA_DATA_wifiScanResults=14
Settings are located in:
root@RAX40:~# cat /etc/Local_RAE_Policy.json
{
"raePolicyVersion": "V0.02",
"stage": "prod",
"reportMethod": "IoT",
"dailyUpdateMethod": "1",
"updaterInternal": "1440",
"routerInfo": "1440",
"routerConfig": "1440",
"readyShare": "1440",
"mediaDevice": "1440",
"connectedDevice": "1440",
"connectedDeviceDetails": "1440",
"wifiAnalytics": "360",
"trafficMeter": "1440",
"internetBandwidth": "1440",
"trafficUsageDetails": "1440",
"eventLogPolicy": [
{
"cpuThresholdHigh": "90",
"cpuThresholdDuration": "60"
},
{
"memoryUtilizationsHigh": "90",
"memoryUtilizationsDuration": "60"
}
],
"enable_trafficUsageDetails": "0"
}
Things changed to enhance privacy
Changes to prevent continuous cloud updates of MAC addresses, connection status, data volumes, ports used, etc. etc. etc even what other wireless routers the unit can hear in the vicinity to avoid channel clashes (i.e. even if you use TOR this unit will accurately reveal your location). As noted above, rebooting has the following deleted directories and their contents reinstated.
rm -rf /opt/leafp2p
rm -rf /opt/xagent
killall leafp2p
killall xagent
The following change prevents a memory leak which causes the router to reboot every 24 hours. Initially I though that wsd (Wireless Status Daemon?) was launched every so often in case it dies (or was killed as it is here). However it seems that terminating wsd once does the trick and it doesn't come back. Even so this won't hurt. The memory leak itself is just poor programming quality. In fact I wouldn't have even considered going to these lengths if it just worked.
vi /etc/contabs/admin50 2 * * 1 /usr/bin/system start auto_upgrade 47 22 * * 1 /usr/bin/system start auto_check 27 * * * * /usr/bin/killall wsd
Firewall rules added to prevent the Bose Soundbar from spamming uPNP on the router.
Notwithstanding uPNP being disabled on at the Nighthawk's interface it still listens via hostapd_wlan0 and hostapd_wlan2 leaving a trail of hanging TCP sockets. One day I'll get to rejigging hostapd....
iptables -I INPUT -p tcp --dport 49152 -j DROP
iptables -I INPUT -p tcp --dport 49153 -j DROP
iptables -nvL
Chain INPUT (policy ACCEPT 2 packets,
96 bytes)
pkts bytes target prot opt in out source destination
25632 1538K DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:49152
25682 1541K DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:49153
66150 22M ACCEPT all -- * * 0.0.0.0/0 224.0.0.0/4
19076 1001K FW_TELNET_ENABLE tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:23
Chain FORWARD (policy ACCEPT 437 packets,
261K bytes)
pkts bytes target prot opt in out source destination
673K 159M ACCEPT all -- * * 0.0.0.0/0 224.0.0.0/4
Chain OUTPUT (policy ACCEPT 91 packets,
18808 bytes)
pkts bytes target prot opt in out source destination
2496 661K ACCEPT all -- * * 0.0.0.0/0 224.0.0.0/4
Chain FW_TELNET_ENABLE (1 references)
pkts bytes target prot opt in out source destination
69 3675 ACCEPT tcp -- br-lan * 192.168.0.7 0.0.0.0/0 tcp dpt:23
387 21948 DROP tcp -- br-lan * 0.0.0.0/0 0.0.0.0/0 tcp dpt:23
0 0 DROP tcp -- eth1+ * 0.0.0.0/0 0.0.0.0/0 tcp dpt:23
Chain PUAC_FILTER_FORWARD (0 references)
pkts bytes target prot opt in out source destination
Chain PUAC_FILTER_INPUT (0 references)
pkts bytes target prot opt in out source destination
Chain PUAC_IMPL_FILTER_INPUT (0 references)
pkts bytes target prot opt in out source destination
0 0 RETURN udp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 67,68,137,138,28053
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 137,139,445,28081,28443
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain INPUT (policy ACCEPT 2 packets,
96 bytes)
pkts bytes target prot opt in out source destination
25632 1538K DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:49152
25682 1541K DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:49153
66150 22M ACCEPT all -- * * 0.0.0.0/0 224.0.0.0/4
19076 1001K FW_TELNET_ENABLE tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:23
Chain FORWARD (policy ACCEPT 437 packets,
261K bytes)
pkts bytes target prot opt in out source destination
673K 159M ACCEPT all -- * * 0.0.0.0/0 224.0.0.0/4
Chain OUTPUT (policy ACCEPT 91 packets,
18808 bytes)
pkts bytes target prot opt in out source destination
2496 661K ACCEPT all -- * * 0.0.0.0/0 224.0.0.0/4
Chain FW_TELNET_ENABLE (1 references)
pkts bytes target prot opt in out source destination
69 3675 ACCEPT tcp -- br-lan * 192.168.0.7 0.0.0.0/0 tcp dpt:23
387 21948 DROP tcp -- br-lan * 0.0.0.0/0 0.0.0.0/0 tcp dpt:23
0 0 DROP tcp -- eth1+ * 0.0.0.0/0 0.0.0.0/0 tcp dpt:23
Chain PUAC_FILTER_FORWARD (0 references)
pkts bytes target prot opt in out source destination
Chain PUAC_FILTER_INPUT (0 references)
pkts bytes target prot opt in out source destination
Chain PUAC_IMPL_FILTER_INPUT (0 references)
pkts bytes target prot opt in out source destination
0 0 RETURN udp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 67,68,137,138,28053
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 137,139,445,28081,28443
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
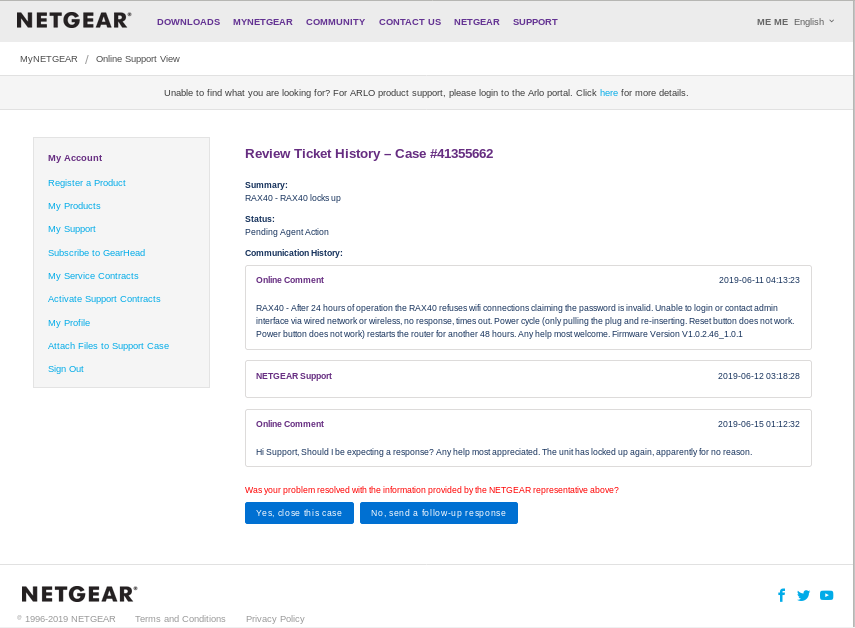
Support
Netgear support responded by simply closing the ticket. There were vague promises via twitter of calling via phone, but that never eventuated