Linux Phone Adventures
This is the evolving story of the development of a phone that won't spy on its user. The story starts in late 2021 on the tail end of the global Covid 19 pandemic. Apple has just announced its phone software will now scan its user's photos for stuff it doesn't like. Furthemore, if the spy program doesn't like what it sees enough it shall inform on its owner to the police, who presumably will investigate and if warranted the justice system shall incarcerate the phone's owner.

2022-01-04 Abandoned Apple iPhone for Ubuntu Touch.
The plan decided on, with the assistance of the informal committee (composed of various experts in their respective fields), was to aquire very highly spec'd yet cheap phones. Obviously that immediately discounts Apple Inc. The manufacturer and model settled on was the Xiaomi Poco M3.
Then once acquired it is to have its operating system removed and replaced. The goal here is simply to provide a degree of privacy. More on that later.
Features
This phone is somewhat special at this point in time because it offers 5G wireless on all Australian carriers networks (which is a different thing to all the SIM brands out there - There are only three networks in Australia). Furthermore it sports an 8 core CPU, it can support 2 SIMs and an SD card. Correction - we actually have one Poco M3 and one Poco M3 pro 5G. These have different CPUs and obviously different radios.

Acquiring the phone was done via Banggood Technology Co., Limited online via their now famous website. The princely sum of $219.58 cents plus all of $0.61 for shipping was paid. I'll let the reader marvel at that price, with the only comment being that it's a mere fraction of the price parted with for the Apple product.
Your Chinese friends won't laugh at you after learning correct pronunciation
Unlocking the bootloader
What is a bootloader and why would it be locked?
To answer this question definitively we'll go back in time to a period in the 1980's when members of the Committee were working in aviation radar tracking and communications and other unmentionable military applications. The old computers (early HP, Perkin-Elmer and General Automation computers) had a special procedure to start them up from power off and nothing useful in their RAM ( core mat in the early GA computers). This was called bootstrapping and its goal is to load the operating system in to memory.
The bootstrapping process consisted of setting some switches on the front panel to indicate an address in the computers memory. Then a switch was pressed to save that. Next the switches were set to indicate a CPU instruction to be executed and which was to be stored at the address just keyed in. Then the write switch was pressed. The switch process went on until enough instructions were entered for a bootloader program. Usually the program was just big enough to get the paper tape reader to read a bigger bootstrap program that could get the magnetic tape reader going. The mag tape held the operating system.
It is worth mentioning the later models gained a new type of chip known as a ROM ( Read Only Memory) which permanently stored the bootloader. Also the later series machines (the range had a 25 year life span) finally got the CPU down to a single large board just before its demise. It was a miracle of miniaturization and the true beginning of the "mini-computer" with 64K to 256K of RAM too!

Here's a video showing the switches in action.
In the context of a modern phone, when the power comes on, fortunately the user/owner no longer needs to key in a bootloader, instead that initial program now comes from semi-permanent storage in a chip. It's role is to go find the main storage and read in the operating system (like Windows or in this case MIUI - Xiaomi's version of Android). Once the operating system program is in memory the bootloader passes over control and your phone springs to life.
Unfortunately many manufacturers like to stop hackers from removing their software and taking over the phone, so they lock the bootloader in to the chip so it can't be replaced and so making it impossible to change the operating system. On the other hand some manufacturers allow this. Xiaomi is one of the ones that does. However, there are certain limits imposed by national governments. In the case of Xiaomi their regulator, the Beijing Bureau of Public Security, mandates certain facts regarding the phones owner be stored on record. Ultimately this is very similar to Apple Inc. which may or may not be directed by the US government in an analogous way. The philosphical aspects around the implications of this are not discussed here any further.
Scams and trojans
The steps needed to unlock the Xiaomi bootloader are both tedious and arduous not to mention time consuming. It is also frought with danger as scam sites abound. Due to the popularity of these models there are literally hundreds of sites that offer advice on how to go about the unlocking task.
Many of the sites are just out of date and following the advice would likely lead to bricking your phone (this includes the Mi community site). Other sites entice the prospective hacker to load a dodgy ROM (note: technically the operating system image which is ulimately loaded into the phone's Flash Memory has popularly become known as a ROM, whereas ROM is the generic name of a type of chip). Clearly loading any old ROM into your phone can lead to your personal information being abused by the ROM's programmers. Other consequences may include providing a path for botnets, and a general path of attack on any device connected to any WiFi network the phone attaches to.
The long and the short of this section is to warn you not to load any old ROM. Also be very careful about loading any necessary tools on to your PC to help in this endevour. And finally, worrying about this aspect will keep you awake at night.
Brick your phone and instantly void the Warranty
Proceeding past this point may damage your phone and your warranty is instantly void the moment you unlock. Xiaomi records the fact you have unlocked the bootloader in their cloud servers, with your agreement and understanding, thereby ensuring you will never receive any further support from them.
Proceeding is entirely at your own risk and ElectricBrain advises you not to proceed with these steps. The information provided here is a record of what happened during the adventure (which hasn't come to completion yet). Your phone may catch fire and be totally destroyed requiring the purchase of a new one (including the SIM). Furthermore you may also find yourself banned from the mobile network too (although I don't know that's ever happened).
You have been warned!
Dear ElectricBrain,
Hello, Greetings from Xiaomi Customer Support! This is Daisy.
We at Xiaomi values your trust and we apologize for the inconvenience.
I understand that you wish to unlock BL. However, if you don't know that much about Android, flashing, custom ROMs etc. It's not recommended for you to unlock the bootloader. It might cause serious damage to your device or personal data. Also please note that maintenance and customer support service of the phone will also be invalid once BL is unlocked.
If you want to unlock BL, I would request you to go to the service centre for professional assistance. If there is no service center in your region, please kindly coordinate with the point of purchase for assistance.
You can find the address of the service centre by referring to the link https://www.mi.com/global/service/warranty/. This warranty will not cover any human damage (physical or liquid damage) encountered on it.
If you have any other questions, welcome to visit again. Always believe that something wonderful is about to happen!
Follow Twitter@XiaomiSupport to get latest product tips and service information. https://twitter.com/XiaomiSupport
Best Regards
Daisy
Verify the phone's provenance
This site was used to verify the authenticity of the phone:
https://www.mi.com/global/verify/#/en/tab/imei
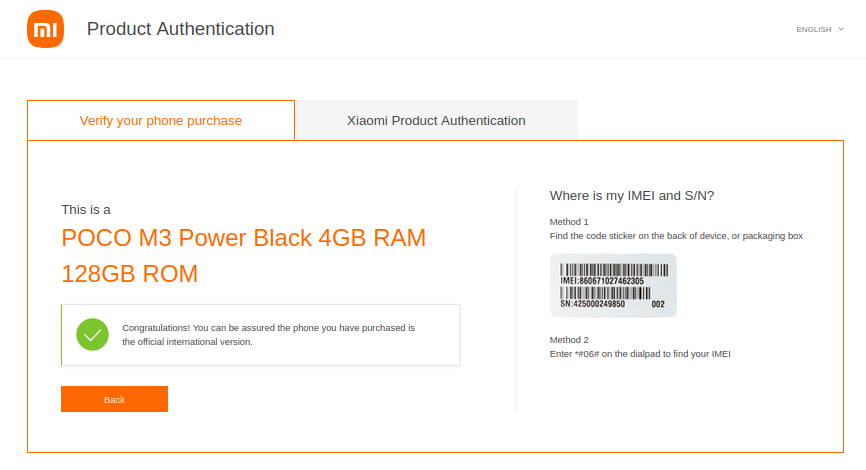
Prerequisites
Essentially the process of unlocking requires a program that communicates with Xiaomi's cloud servers and the phone. The phone can't unlock itself since it can't talk to it's own debugger, only an external computer loaded with the correct software can do that. The program collects vital identifying information and stores it against your Xiaomi cloud account. This process ensures the phone will no longer receive any further support effectively locking off the Xiaomi support network.
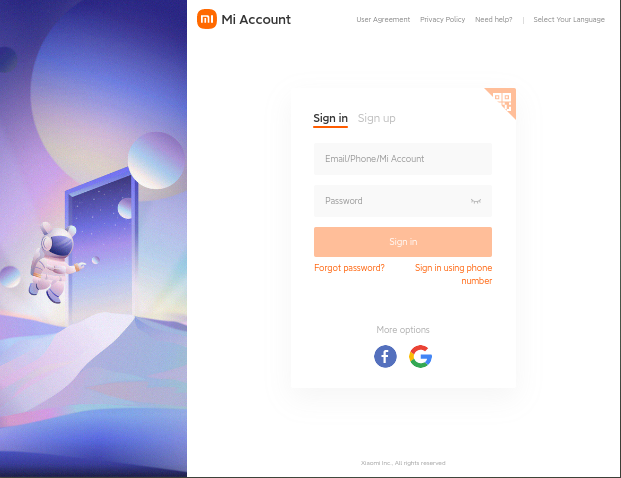
Establishing an identity with Xiaomi means creating an account on their servers. That account, for most people world-wide, means saving information in a foreign country. In general that information becomes subject to the laws of that country or jurisdiction as well as those in your county. It's up to the reader to understand the scope of people and entities that may have access to the account information. It is not possible to unlock the phone without a valid Xiaomi account.
Once the account is established the next step is to add the device. The Xiaomi site is very well organised so that part of the process is not covered here.
Having established an account it is then necessary to log the phone in to the new account.

The final step is to ensure Xiaomi's cloud servers have full access to all information held on the phone, its SIMs and anything else it can get its hands on. As this phone is brand new it has no personal information loaded yet, apart from the SIM phone number, geolocation and WiFi details.
Once these steps are complete Xiaomi will instantly know as soon as you have unlocked your phone. Furthermore the company will then allow you to begin the steps to unlock.
Establishing the PC environment
Here at ElectricBrain the approach has been to treat all supporting desktop computer software as if it were infected. Imagine the analogy as being a Covid19 infected patient in a hospital. To that end two environments were established. One being a Linux docker container and then finally a freshly downloaded Windows 10 environment running in VirtualBox. The reasoning here is that any infection is confined within the container or virtual machine while the host desktop computer escapes unharmed, a PPE (Personal Protective Equipment) of sorts.
The unlock program itself needs to be correctly installed and must be downloaded from a trusted source. Be careful not to (as was initially done here with the Linux program) download from a scam site. It is very easy to infect your computer, hence the advice to isolate any downloads before running anything. The linux trojan unlocker was isolated and no harm was done. However, it is possible the Xiaomi account password was stolen (which doesn't really matter since the account is a "burner"). This serves an an example of just how dangerous this process is. Obviously the consequences of running such a program directly on your PC could be catastrophic. In the limit you could be running a crypto-locker destroying everything it can find and resulting in you being held to ransom.
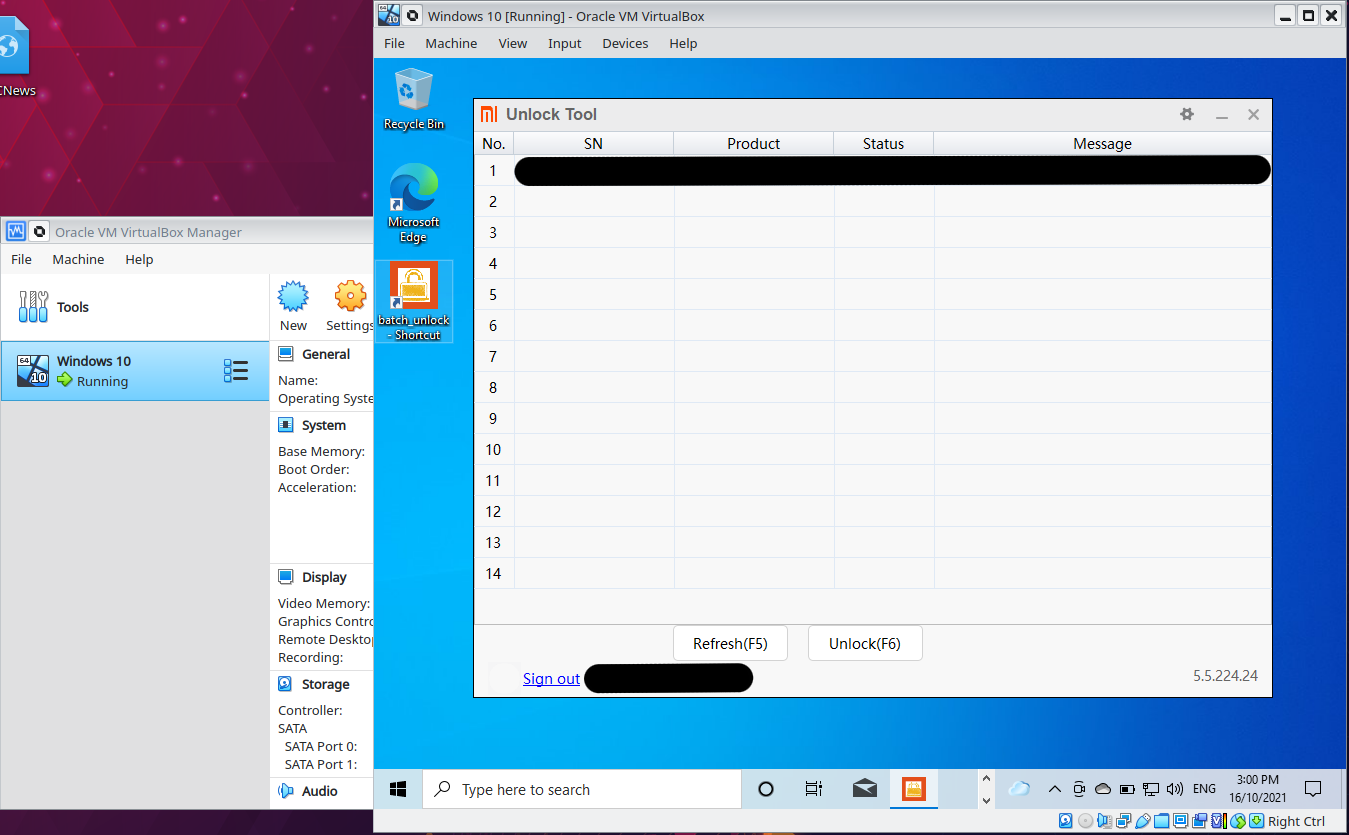
Windows 10 running in VirtualBox isolating any evil software from the host system
Similarly Linux inside a Docker Container making use of the isolation capabilites to cordon off any nasties
Xiaomi does not appear to provide anything other than Windows software to support their range of phones which is kind of odd since Android is actually a derivate of Linux. There are Linux equivalents with XiaoMiTool V2 (by Francesco Tescari) one which appears to work - available on GitHub.
Beware of scam sites offering V1 (very likely trojans), with its onerous java setup requirements, and which no longer works.
It's also pretty clear from comparing the Windows screenshot above with many other sites showing the old Mi_Flash program performing the unlock operation, that these sites are badly out of date. Likewise, there is no doubt this page will also decay in revelance with the passage of time. Check the dates and the facts as you go. The time of writing is mid October 2021.
VirtualBox is your friend

Rendering the unlock and ROM reflashing process safe hinges on isolating potentially harmful software from the underlying computer running it. To that end it is vitally important potential phone hackers (you) invest in the time to install an effective isolation barrier.
Having said that, if this page starts covering the installation and setup of VirtualBox it may be that page construction will never end. Go to the VirtualBox site and follow a guide to install it on your computer.
https://www.virtualbox.org/
Likewise Docker installation is also currently out of scope at this point. The base image used here is:
https://hub.docker.com/r/kdeneon/plasma
Burner Windows environment
The notion of a "burner" environment simply means disposable. Once the unlock process has taken place the entire environment can be deleted, providing a further degree of safety if it is suspected something has become infected. Remember this is not about hiding identities, it's only about shielding the host computer from the potentially hazardous environment.
Download the Windows 10 official ISO from here:
https://www.microsoft.com/en-au/software-download/windows10ISO
Then follow this guide Install Windows 10 On VirtualBox Virtual Machine: How to Guide for installation instructions. Alternatively use your favourite search engine for a suitable guide.
Burner Docker KDE environment
![]()
Well maybe not a burner as this is the personal preference for a daily driver environment to talk to the phone. As an alternative to Windows this environment is something of a work in progress and is clearly waaaay more complicated to get running. At this point the build and run files are shown here as is (you know no warrantly, your own risk etc. etc.). Note that the cross compiler infrastructure has been added. This is to allow for compiling Xiaomi's kernel source (which was the subject of a 10G download thankyou very much). More on that later.
The build script
#!/bin/bash
#
# Build the latest image of KDE Phone dev
#
# Settings
#
pwd
set -x
set -e
. settings-global.inc.sh
. settings.inc.sh
lcFromImage="registry:5000/kdeneon/plasma:20210815"
# Cleanup
#
set +e
docker rmi "$gcRegistry/$gcImageName:latest" 2>/dev/null
docker rmi "$gcRegistry/$gcImageName:base" 2>/dev/null
docker rmi "$gcRegistry/$gcImageName:$gcVersion" 2>/dev/null
set -e
# Create the Dockerfile
#
cat << EOFZZZ > context/Dockerfile
FROM $lcFromImage
maintainer xxxxxx <xxxxxx@electricbrain.com.au>
RUN /bin/bash -c " \
id; \
sudo apt-get update ; \
sudo apt-get install -y --no-install-suggests \
binutils-aarch64-linux-gnu \
gcc-aarch64-linux-gnu \
adb \
fastboot \
openjdk-11-jre-headless \
openjfx; \
sudo usermod -aG plugdev neon; \
"
COPY environment /etc/environment
EOFZZZ
# Build the image
#
docker build --no-cache -t "$gcRegistry/$gcImageName:$gcVersion" context
docker images
The environment needed to get Java working. Version 1 of XiaoMiTools needed this. It was done before discovering version 2... doh!.
PATH="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin" JAVA_HOME="/usr/lib/jvm/java-11-openjdk-amd64" JAVAFX_HOME="/usr/share/java/openjfx"
Container run script
Xephyr -screen 1680x1050 :1 & \
docker run \
--rm \
--name=android-dev \
-v /tmp/.X11-unix:/tmp/.X11-unix \
-v /docker/private/myhome/Xiaomi_Kernel_OpenSource/root:/root \
-v /docker/private/myhome/Xiaomi_Kernel_OpenSource/home/neon:/home/neon \
-v /media/nfs/nfsstorage/programs-applications/Hardware/Xiaomi-Poco-m3/:/hardware/Xiaomi-Poco-m3/ \
--device /dev/bus/usb/001 \
registry:5000/kdeneon/plasma-phone-dev:ku20-amd64-1.3; \
ps -C Xephyr -o pid= | \
xargs -I{} kill -SIGINT {}
(Note to self: explain what Android's USB fastboot, ADB, file transfer, PTP modes are.... somewhere...here?)
Gathering the necessary tools
One of the first tools that needs to be loaded is a "driver". This driver, loosely termed since the operating system doesn't actually use it, enables communications via USB cable with the phone and is required for Windows. Linux doesn't need such a thing since the "driver" is actually loaded and built in.
Curiously with that said the Windows driver appears to be specific to the manufacturer or so some web sites would have us believe. It is certainly true that Windows refused to talk to the phone when it was booted up in Fastboot mode. After signing up with Qualcomm, the manufacturer of the Snapdragon 662 used in the Poco M3, it became clear the official driver does not come from them and they confirm that it is supplied by the device manufacturer, in this case Xiaomi.
The official Android developer site has advice on locating the needed drivers too.
https://developer.android.com/studio/run/oem-usb
All official advice is to go to: http://www.xiaomi.com/c/driver/index.html for official drivers. DO NOT download and install drivers from some random site!
Lots more stuff to go here.....
Unlocking
Finally, after waiting the required 7 days.... the dreaded wait message was gone. Pressing the Unkock(F6) button set the phone off on its journey to freedom and privacy.
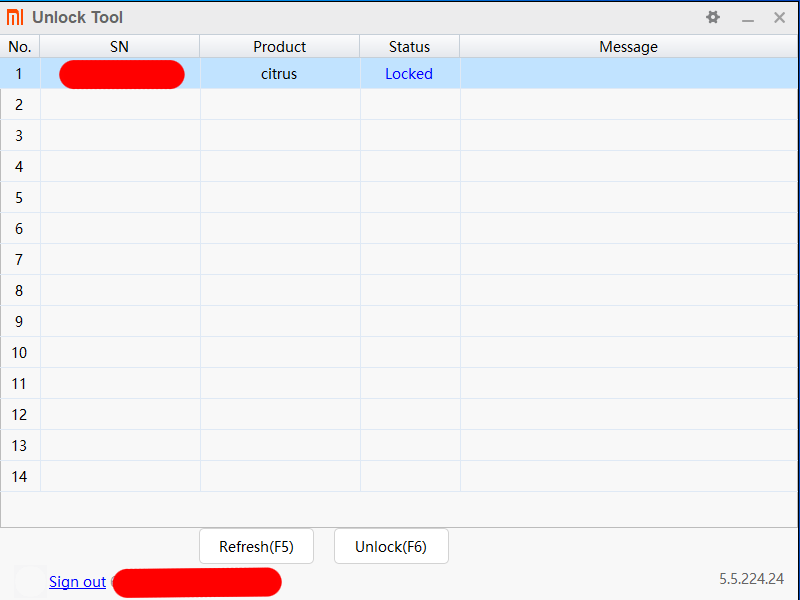
The phone immediately set about wiping all existing data and then factory resetting. Everything must now be repeated except this time don't allow any further syncing to anywhere for any apps. I assume that the unlock code could possibly be used to identify the phone, which is something of a moot point as the operating system is about to be removed.
Don't be too worried if the phone sits and the MIUI screen for a few minutes. It seemed to be thinking very hard about something but then it finally booted. This one has a burner SIM in it too, so if anyone works out the phone number it's now in the Australian carrier Optus's "deadpool".
To progress further the phone must be connected to a network (WiFi or mobile) so that the Xiaomi cloud system can verify the account password - i.e. you have not stolen this phone and the Beijing Bureau of Public Security knows this IMEI (there are two - one for each SIM) is now a candidate for intensive tracking, a fact which may or may not be shared with other govenments.
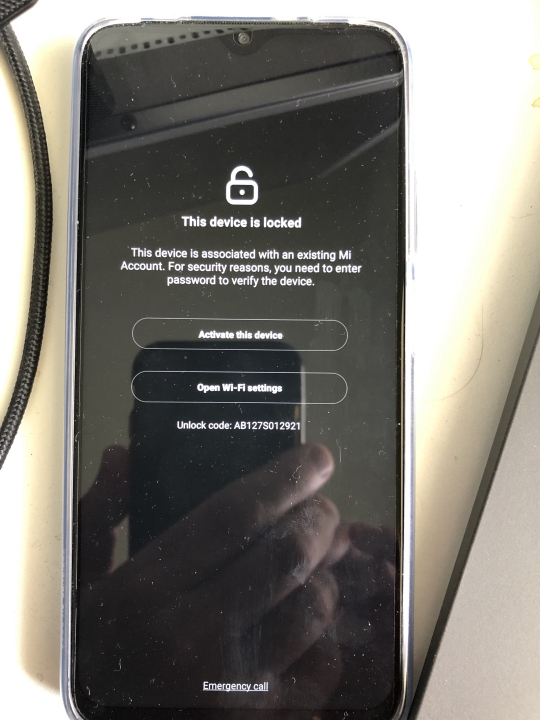
Unlock confirmed - zero support from now on
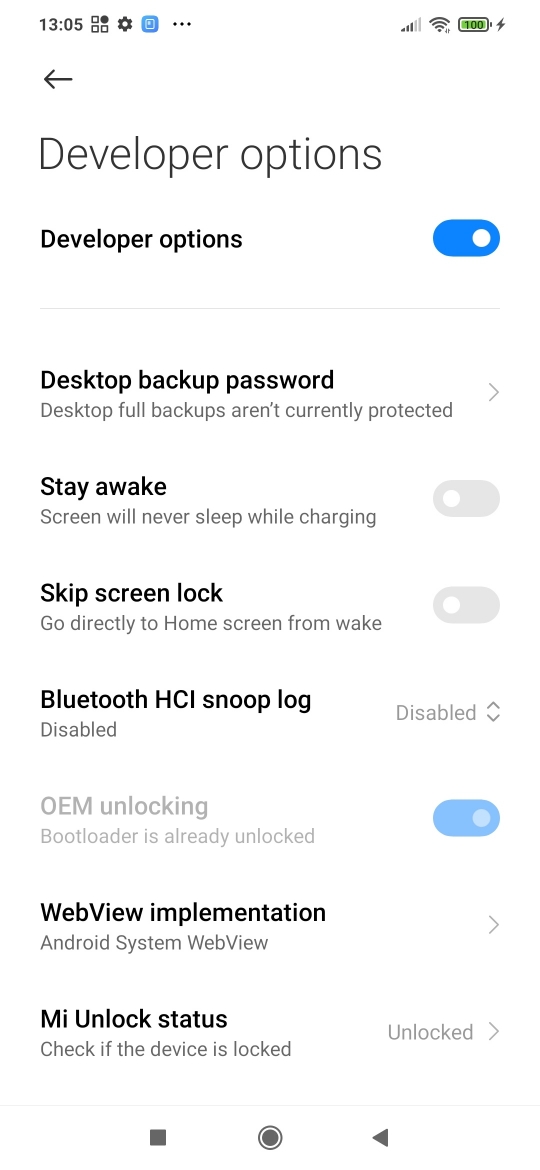
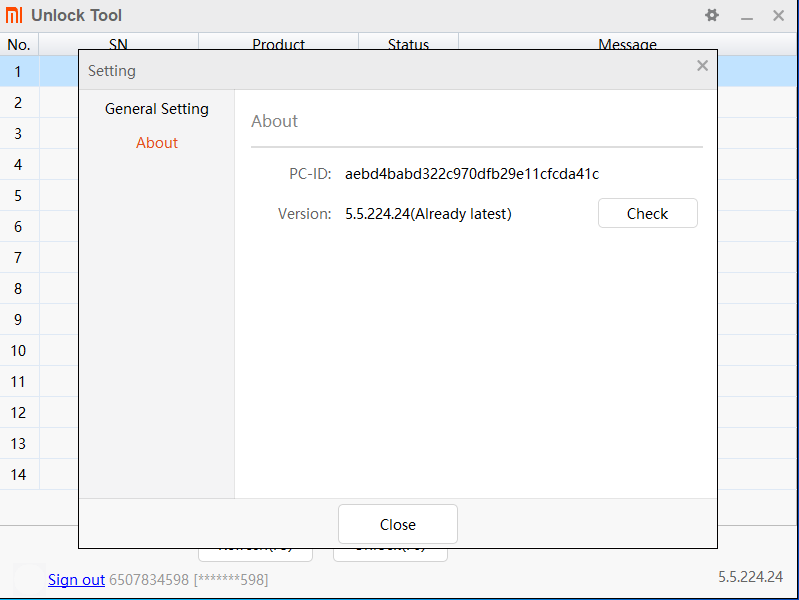
Xiaomi has recorded the PC's details
Prospective unlock program users should be aware Mi Unlock Tool collects and stores identifying information about your PC in the Xiaomi cloud. This is a further example of gratuitously collecting personal information for no reason. Anyway the burner virtual PC's id is presented here for all to see. If anyone can workout any serial numbers please let me know.
By using fastboot mode and asking the phone for its product-info we get (both Windows and Linux):
fastboot oem device-info (bootloader) Verity mode: true (bootloader) Device unlocked: true (bootloader) Device critical unlocked: true (bootloader) Charger screen enabled: false
Android Verity Boot
This now raises the next point which is sure to frustrate budding ROM developers: Later versions of Android, including Xiaomi's MIUI version, now include Android Verified Boot. Essentially Android now cryptographically verifies all code before executing it to check for signs of tampering. The above fastboot query shows Verity mode: true meaning the function is active. Obviously MOSAD, FSB, CIA, ASD, BPS etc etc have been very busy corrupting and hacking peoples Android phones and to Google's credit they took action.
At this point it is clear that this page must come to a successful close and another started. Thankyou for reading this far. The journey is far from over. Preliminary ROM uploads have succeeded with UBPorts Recovery operational, however, it has hit a snag, which at this time is suspected to be caused by the new-ish AVB. UBPorts is currently blocked. While the phone is not currently operational as a phone, it is definitely not bricked!
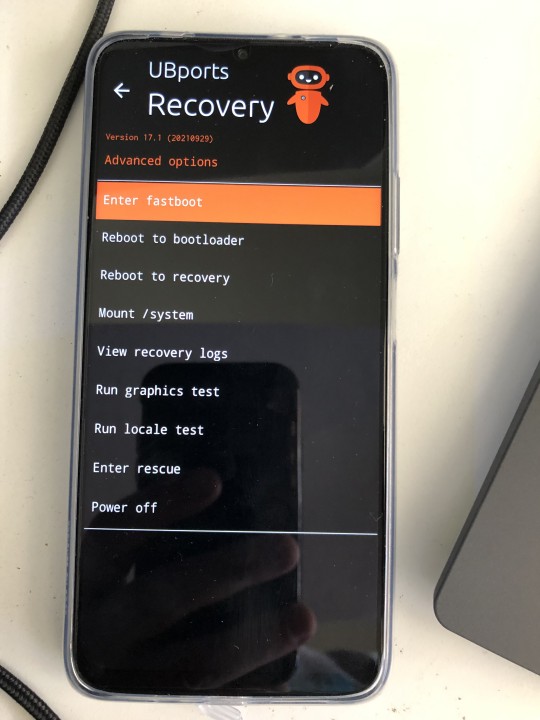
Success thanks to the folks on XDA. Without their help the project would have stalled badly. I can't say enough about how helpful people are.
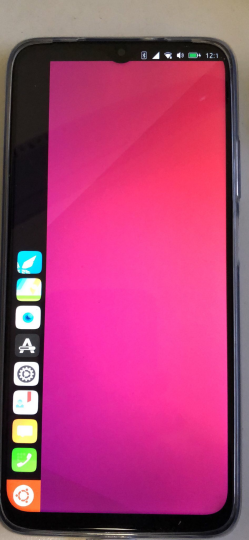
The adventure continues with the description of the installation of Ubuntu Touch and various things learned along the way.
.... this page is no longer under construction.... updates and stuff will be added periodically however.