
Lets Encrypt free HTTPS now activated
Free TLS https certificates which activate the lock icon on your website. Evil doers will now have to work harder to listen in on communications coming and going from your website offering users enhanced privacy.
The ISRG (Internet Security Research Group) based at 1 Letterman Drive, Suite D4700, San Francisco, CA 94129 are behind this initiative. Their website ( https://www.abetterinternet.org/about/) describes who and why they have been providing this service. "Our mission is to reduce financial, technological, and educational barriers to secure communication over the Internet."
Well FREE is pretty darn cheap and it certainly fits within the price range here at electricbrain. I remember all the fuss we used to make at my old place of employment about the SSL certificates. And then they would expire. Nobody ever remembered to get new ones before expiry, so the site always went down. Accounts would receive the notices but who knows what happened from there.
These days the process of obtaining the necessary certificate is free and fully automated. Here's how it works.
The key points in a nutshell:
- Free as in free FREE
- (plus) No annual payments
- (minus) Short 90 day life
- (plus/minus) Automation is essential - enter certbot
- Fully dockerized standalone implementation described here
- Alpine Linux
- Standalone "Virtual Machine Image"
- Hourly certificate update checks
- Automatic swarm managed container deployment via Portainer
- electricbrain webserver now using HTTPS
- Unencrypted login disabled via HTTP
- Some content only available via HTTPS
Certbot is EFF's automated program which talks to www.letsencrypt.org to retrieve free certificates.
Usually certbot is loaded on the same computer as the webserver making for ultra simple two step installation. Here the setup is complicated by the reverse proxy server plus a backend server per site.
This implementation is a dockerized build and deployment based on Alpine Linux 3.11. However instead of using the Alpine package, everything is compiled and built from the sources. At the time of writing Alpine list their package as version 1.0.0 for Arm64. The sources used here are the current 1.3.0 stable branch. (note: the downloaded sources did not compile due to using out of date Zope package versions. The fix is to change the versions and the checksums to the current versions visible on the web)
Update 2024.05.29
Currently hub.docker.com has a bunch of "authorized official" containers from EFF. The home built containers have been retired now. The official containers are now successfully interacting with Cloudflare DNS servers and updating the SSL certificates here automatically.
Security is enhanced by separating Certbot out to its own docker container which is not accessible to the outside world. It does its thing every hour from one of the nodes (Portainer deciding which one) updating any stuff that needs doing.
The resulting certificate is then shared with front-end reverse proxy machine via an NFS share. The reverse proxy is another standalone docker container running what is in effect another virtual machine (bear in mind the arm64 CPU does not support virtualization which is what makes Docker so wonderful).
The reverse proxy machine itself is isolated from the Certbot credentials and only has access to its own certificates. The file structures shown below are mounted in to the virtual computers to make them look like local directories on their hard disks.
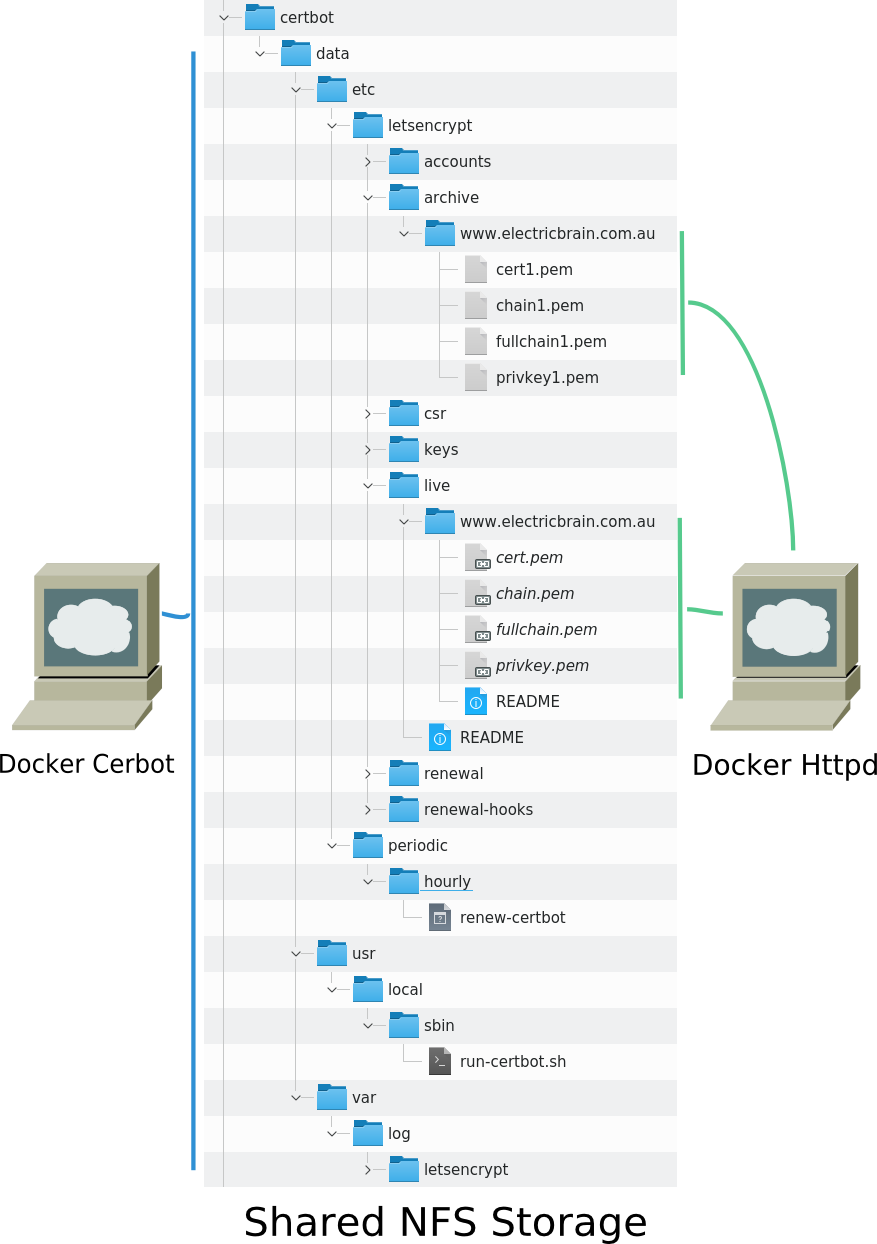
Certbot also needs a reverse file share from the web server in order to prove to the Let's Encrypt server that it actually has control over the domain. Let's Encrypt's ACME protocol asks certbot to place an encrypted challenge response file in a "well known" directory. LetsEncrypt then makes a web request to the site looking for the response file.
Confirmation is achieved when Let's Encrypt is able to retrieve the file. If it does, all is well and a certificate is granted. Certbot then deletes the file and cleans up, moving on to the next step in the process.
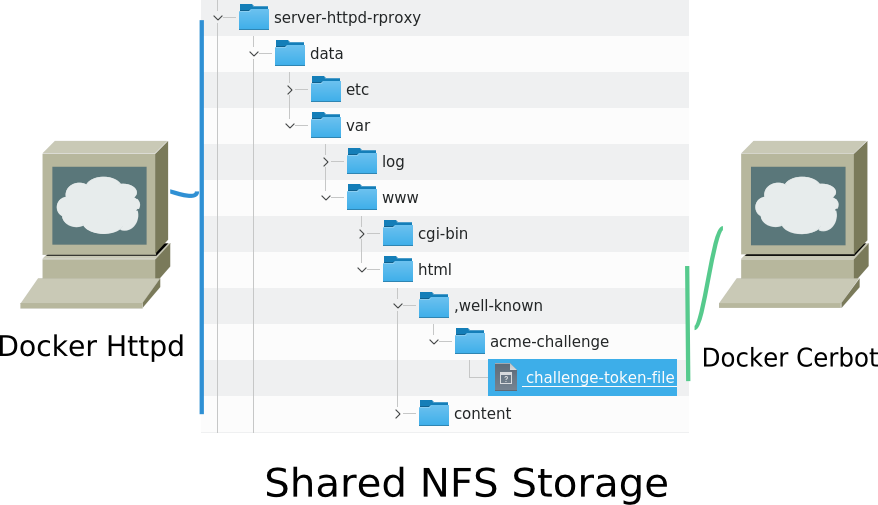
At www.electricbrain.com.au it's slightly more complicated because the server providing the content is not the same computer using the certificates. The reverse proxy machine does not serve content, it merely passes on external user requests, encrypting and decrypting communications with the outside world, applying access control and logging requests for the analytics. Each site has its own backend server(s). For the purposes of the ACME protocol an exception is made so the "well known" directory is actually served from the front end machine
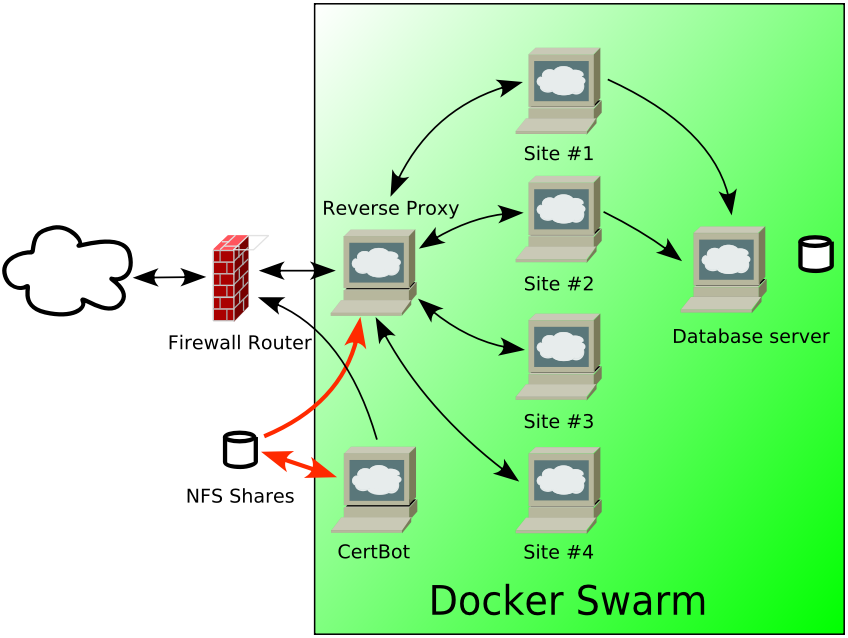
All fully automatic with no human intervention.
